A blockchain technology solution connecting the transportation ecosystem 
Our client, a roads and transport authority of a country in the middle east, had to address the challenges of using a legacy system by the police department that caused delays in reporting rental activities data to the rest of national security authorities. Besides there were multiple systems operating in silos resulting in duplication of data. Chainyard, as a prime partner for blockchain solution implementation, developed a de-centralized repository for every rental activity across cities. 
The new blockchain-enabled solution is expected to improve revenue collection, enable & empower agencies, and more importantly increase customer trust significantly. 
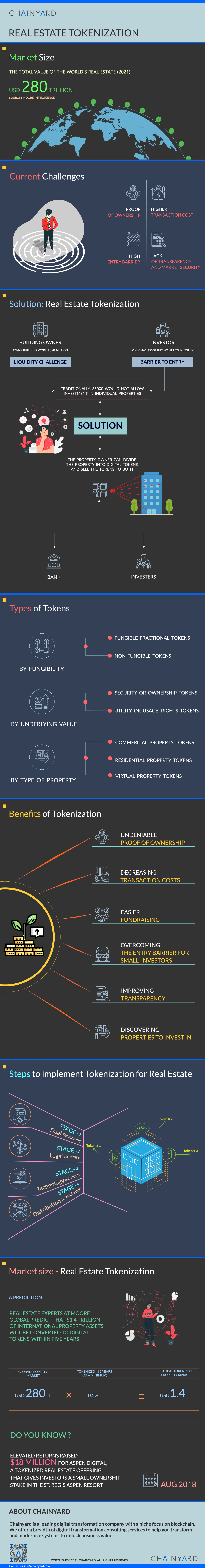
Real estate tokenization enables the modern-day concept of fractional real estate ownership. Additionally, it helps overcome investment barriers and reduces associated risks and costs. Solution providers in this domain help real estate investors navigate through the various stages of ÔÇô Deal Structuring, Legal Structuring, Technology (e.g., blockchain), Distribution, and Marketing.
The following infographic provides a snapshot of the current market, its potential, and expectations, along with the process, benefits, challenges, and solutions.
Read more here:
Transforming the business of Real Estate Assets through Tokenization
Real Estate Tokenization: Implementation Process Steps and Key Outcomes
Software license management (SLM) ensures that the software licenses in use are valid, to prevent the free use of proprietary software. It is a proactive practice aimed at preventing or minimizing software copyright violations both at an organization level and for a common user. License validation is a prerequisite for software installation.
The common ways to distribute licenses are:
Software license validation methods serve as control measures to ensure that software publishers are compensated. Software license audits are a reactive practice aimed at rectifying situations of non-compliance. It provides greater control and cost savings while ensuring efficiency in software distribution besides being a preventative mechanism for copyright infringement.
The global software asset management market size is expected to grow at a Compound Annual Growth Rate (CAGR) of 18.1%, from USD 2.0 billion in 2021 to reach USD 4.8 billion by 2026. (Source)
Managing software licenses follows a pre-defined and widely used set of procedures. The process involves:
The process of software license management includes a few steps such as:
Implementing a Blockchain system for software license management can improve the traceability of software licenses throughout their lifecycle- from purchase to allocation, to decommission. The ledger is updated based on the transactions on Blockchain, to provide a real-time view of available assets and the distribution of used assets. The system can also help to map the systems that use specific software or even functionalities within it.
Blockchain is an excellent tool for creating, managing and storing licenses and licensing information. Its decentralized data storage and peer-to-peer computing network help implement any logic in smart contracts. The four most important benefits of Blockchain technology are:
Blockchain becomes relevant for SLM with its log of transactions where information is stored in a distributed, decentralized manner and is accessible to everyone.
Blockchains are a natural fit for storing the sale and terms of routine licenses such as producing and distributing e-books and self-executing contracts that could include (or exclude) resale of the rights. Blockchain licensing enables trust, regulation, and monitoring while deciding which transactions are to be recorded. Blockchain can provide access to the public about updates in the reversal of rights back to a creator, or transfer to a new agent, or other recorded rights.
A Blockchain system for SLM can prevent the installation of software when no licenses are available, thus preventing over-utilization. Some of the other operational features of Blockchain in SLM are:
Blockchains are unlikely to be of much use in mitigating ordinary infringements in software licensing. There could also be difficulties with the areas of custom licensing and scalability. Work needs to be done on blockchain technology and to establish a trusted link between the blockchain and established infrastructures and data sources.
Getting software usage data from the organizations is a difficulty as most of the organizations are operating their servers behind a firewall and usually their security practices do not allow software metering clients on their servers to send out data.
Blockchain can reduce costs, increase operational efficiency, improve transparency, and facilitate a range of innovative possibilities such as:
Blockchain for enhanced asset management – One of the major solutions in this space is designed to provide industry-leading asset management capabilities. Traditionally, asset-related transactions are shared across a business network using interfaces between different systems of each party involved. Third parties carrying out work on a customerÔÇÖs assets often use systems that are isolated. In some industries, regulators are looking for customers to proactively demonstrate compliance. It helps mitigate the challenge of communicating with multiple parties on connected systems.
More than 30% of software on machines tested worldwide was unlicensed according to 2021-22 statistics. (Source)
Blockchain typically finds uses in License management in these areas:
ChainyardÔÇÖs certified team brings extensive experience to architect, build, test, secure and operate solutions that help blockchain adopters succeed.
The solutions include:
ChainyardÔÇÖs blockchain consulting team uses a growing set of solution accelerators. The accelerators provide:
Many instances of cyberattacks have demonstrated that smart contracts, like blockchain technology, are vulnerable to hacks and exploitation. The total amount of money stolen or lost as a result of smart contract errors is in billions of dollars. The following are some of the most significant instances of smart contract code errors:
Smart contracts are self-executing contracts, in which the provisions are stipulated in the code.
For example, an Ethereum smart contract is deployed as one or many transactions on the Ethereum blockchain which then runs on the Ethereum virtual machine, a blockchain-based platform.  The smart contract can be called by a user, by using a blockchain transaction. This transaction calls for a pre-defined procedure on the smart contract, granting the user access to the information contained within it.
For example, a vending machine operates on ÔÇ£contractÔÇØ logic. The operation of dispensing a product is only fulfilled when a user puts money in the machine and chooses the product. Smart contracts are, of course, employed in a more complex manner when conducting cryptocurrency transactions.
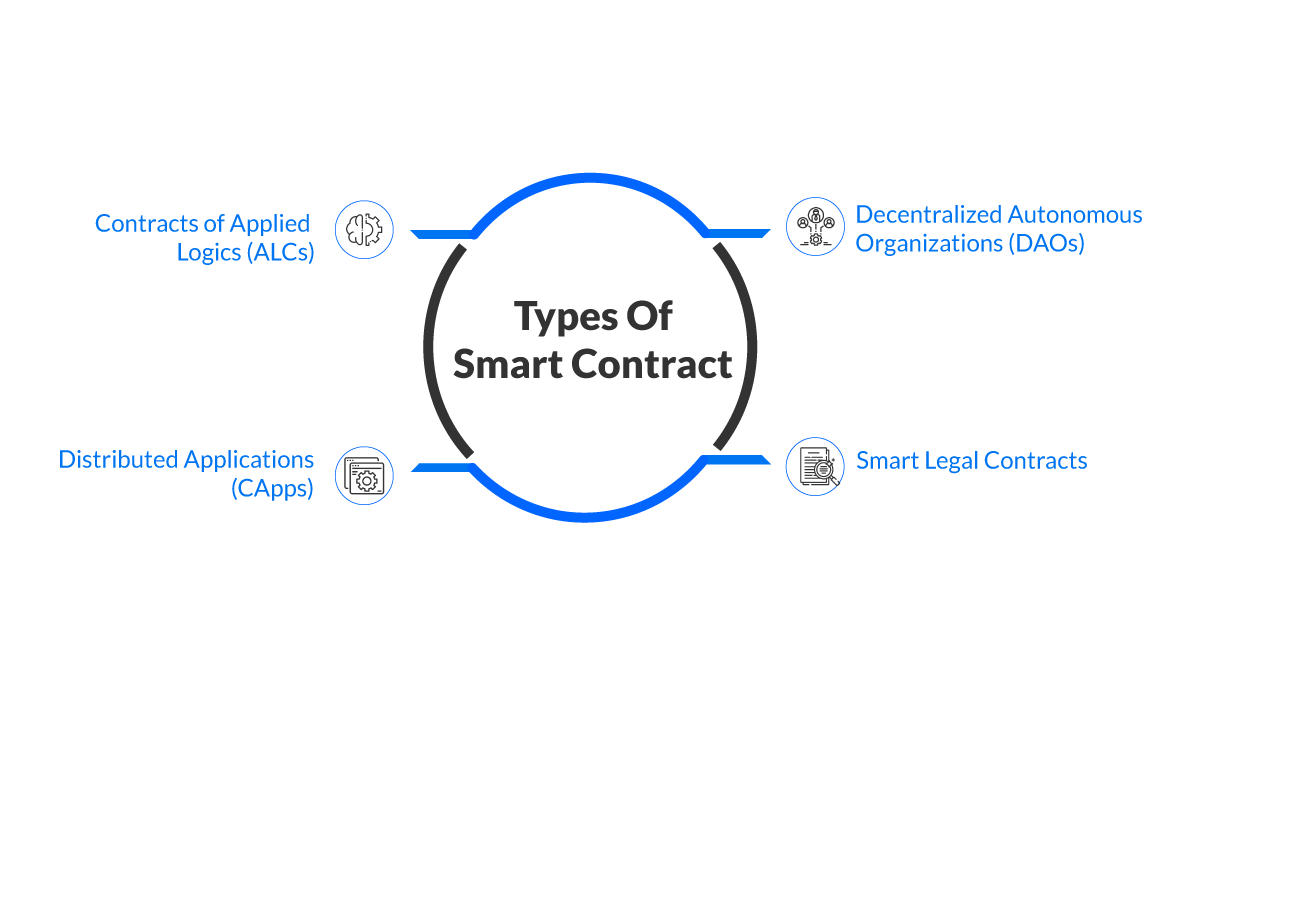
Smart contracts are designed, constructed, and deployed over a network using programming languages like Solidity and Vyper. Smart contacts come in varied flavors, some of the most used types are –
Solidity contracts tend to transfer significant amounts of value as one of their core functions, in contrast to many conventional programming languages. As a result, they are vulnerable to several high-risk attacks from attackers looking to siphon money from these immutable actors.
Let us quickly review the main vulnerabilities:
As a result, if a vulnerable contract X makes an external call to an untrusted contract Y, the latter may be maliciously modified to make a recursive call back to the weak contract X. Contract X might essentially run out of resources before the function is finished if the call from contract X to contract Y includes transmitting any amount of ether.
One unintended consequence of this design is that a smart contract’s intended conclusion is publicly visible before it is validated onto the blockchain. This transaction might be seen by malicious actors scanning the mempool, who might then take advantage of the situation by copying your smart contract and submitting it at a higher value. Then, by submitting their transaction first, they have successfully “front-run” your contract, taking advantage of your arbitrage opportunity.
There are other security obstacles that smart contracts must face in addition to those mentioned above. Smart contracts are frequently vulnerable because not all developers are versed with the semantics of programmable blockchain systems.
In the upcoming blog, we will also be covering key processes involved in securing smart contracts and recommendations at different levels while developing a smart contract.
Asset tracking is a key business processes for many large enterprises and involves many partners operating independent systems, each with their own view of the asset. Blockchain is a perfect choice to solve the complexities of siloed systems by capturing the status of the asset throughout the life cycle as the asset moves from party to party in the supply chain. Learn how we collaborated with our client, a global IT services and solutions provider, in designing and implementing a blockchain based solution that has created a single source of truth for all partners across the supply chain.
As enterprises look to improve communication and relationships with their suppliers, the process of on-boarding and maintenance of suppliers becomes a stumbling block due to fragmented information sources and technological gaps across the stakeholders. Locating quality suppliers and assessing regulatory risks becomes a cumbersome, time consuming process, while there is also a duplication of data when each supplier provides their information to each customer. Learn how we created a blockchain network with confidentiality practices to bring together like-minded companies ÔÇô buyers, suppliers, auditors, certificate issuers, and other third parties ÔÇô to form this next-generation blockchain network.