The internet was created without a native identity layer and different Internet solution providers have developed ad hoc identity solutions that are inconsistent. With billions of people now online, the drawbacks are more apparent, more so with the emergence of Web3. Decentralized Identifiers (DID) are globally unambiguous identifiers that can be used to identify any subject (e.g., a person, an organization, a device, a product, a location, or even an abstract entity, or a concept) and enable secure online transactions. DID is a new type of verifiable identifier, which does not require a centralized registry. DID enables the controller to verify ownership of the DID use cryptography while ensuring security.
W3C Decentralized Identifiers are portable across service providers and can last for as long as their controller wants to continue using them. DID can also be used as a tool to verify professional documents, including passports and driverÔÇÖs licenses. Users can securely navigate across a variety of platforms with DID with a consistent identity for their wallet and personal information.
DID solutions can help uphold the integrity of usersÔÇÖ data and provide new safeguards for users. They can verify identities, authenticate traceability, validate digital assets, and enhance the overall security of the internet. DID applications can help users successfully control and manage their own digital identities, where they can log in securely to different systems without exposing their privileged information.
The decentralized identity market size is expected to grow from USD 285 million in 2022 to USD 6,822 million by 2027, at a Compound Annual Growth Rate (CAGR) of 88.7% (Source).
Additionally, one-click login & onboarding with identity verification was the application that most people (57%) felt the need for decentralized digital identity among Web 3.0/DeFi implementations in a 2021-22 survey (Source).
Web3 requires a critical degree of security throughout the ecosystem to ensure its full potential so that every transaction is accurately recorded and cannot be altered. Without DID solutions, there is a risk of users losing their sensitive valuable, and confidential information to hackers and fraud.
The adoption of crypto and advancement across Web3 has increased rapidly but there are still significant barriers that stand in the way of mainstream adoption. DID can address some of the current Web3 pain points related to:
Nonfungible tokens (NFTs), Identity and Authenticity issues, fraud, and plagiarism threats affect artists or creators. An example is a work of digital artist Derek Laufman (designer of Marvel superhero stories) being auctioned on NFT platform without his knowledge. To counter such issues, applications can be built on DIDs to allow creators to prove that a given NFT was created by them. Buyers and sellers can verify the authenticity of digital artwork.
Growth of Decentralized Finance (DeFi) – Collateral requirements limit most cryptocurrency traders looking to take advantage of leverage. Reducing or completely removing collateralization requirements would enable mass adoption of DeFi. The DID layer can provide users with credit-based loans and help users directly control their own credit scores, better monitor, and adjust their own lending behavior. So far the identification has been issued by the government. With DeFI we need a global level of identification and KYC.
KYC and other identity controls could change DeFi by allowing regulated entities to participate as intermediaries, directly and indirectly. DeFi protocols could enable trusted third parties, like identity providers, to perform the KYC.
Decentralized Autonomous Organizations (DAOs) use token-based governance for voting, governance, or prioritization but it can preclude or de-prioritize active contributors without significant capital. Each DAO member of the hundreds of DAO needs to build their reputation within, only through participation. DIDs can help users maintain their reputation across multiple DAOs. Porting credentials from one DAO to another is easier with DID.
The DID specifications are based on foundational pillars. DID metadata is resolvable and can be discovered. DID are:
The DID ecosystem is made up of layers, with each layer on the top, building upon the underlying protocol. It includes:
W3C Decentralized Identifiers and W3C Verifiable Credentials are used across several markets where identification and data authenticity are a concern:
The Retail and the E-commerce sector have seen rising digitalization, outlining the need for increased authentication given the complexities in data systems. Convenience stores, grocery stores, restaurants, bars, and consumer goods companies can use DIDs for new digital age verification programs to increase privacy and checkout speed, prevent unauthorized data access, reduce data losses and eliminate the use of fraudulent identity documents during purchase.
The Financial Services industry depends on identity verification to check illegal activities such as bribery or money laundering. DID can help refresh KYC processes by allowing for the effective outsourcing and decentralizing of personal data, while also allowing the owners of the data to retain full control over it. DID can help in the shopping and purchase of insurance products, finance and credit products, e-finance, and cross-border remittance.
According to Forbes, major banks each spend up to USD 500 million on cybersecurity every year, with USD 25 billion being spent in the US on AML compliance. Source
Governments ÔÇô Government agencies in the US, Canada, and EU are exploring the use of DIDs to provide privacy-protecting digital identity documentation for their businesses and residents, enabling them to choose how and when their data is shared.
Supply Chain operators and stakeholders such as global government regulators, trade standards institutions, vendors, shippers, and retailers use DIDs to design systems that verify the origin and destination of products and services accurately. This will streamline and enable the reporting and documentation to apply correct tariffs, prevent dumping, and monitor transshipment.
Personnel and Workforce ÔÇô Universities, education standards organizations, and training programs use DIDs to issue digital learning credentials when applying for higher education or workforce positions.
Being a key technological foundation to support native Web3 applications,  World Wide Web Consortium (W3C) has declared that Decentralized Identifiers (DIDs) v1.0 is an official Web standard. This verifiable identifier enables both individuals and organizations to take greater control of their online information and relationships while also providing greater security and privacy.
Robust DID solutions can help Web3 to go mainstream by enabling new use cases. The composability and interoperability of DID standards help the momentum created from each new application feed on another. DID solutions having been declared an official standard by W3C we expect it to grow rapidly in the coming years. The presence of service providers can unlock the next major cycle of Web3 applications and the value therein.
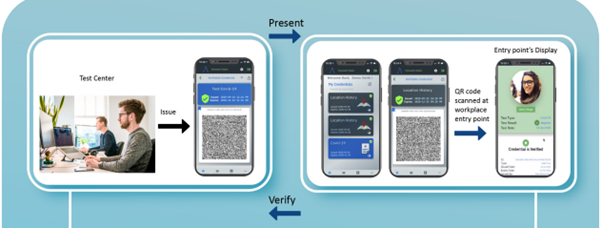
Chainyard has firsthand experience in building to W3C DID standards. The health wallet app is an example of its capabilities in this space while its use cases provide detailed insights about its projects along with sample UI/UX development. Chainyard is an innovator in blockchain and distributed ledger applications, and the owner and creator of Trust Your Supplier. The first Chainyard initiative in this space is the innovative MyHealth Wallet application, available on Android and iOS. It provides the user with a simple, tamperproof, and verifiable way to present and prove that they have taken a COVID-19 test.

The second in the family is the Trusted Health Checks mobile application that combines human validation and ML-generated risk scores and allows visitors to complete electronic health declaration forms prior to travel to foreign destinations.
Decentralized Identifiers (DID) has a key role to play in healthcare since it (healthcare) is now a collection of information spread everywhere across different doctors in multiple specializations, the emergency room, and other facilities. With DID patients can own and control their healthcare data.
In the absence of DID, coordinating, sharing, and working with one set of data can be difficult apart from the process of authentication that needs a unique identity for everyone. The entry of a new wave of decentralized identifiers (DIDs) and verifiable credentials (VCs) data supported by blockchain makes it possible to achieve decentralized entity authentication.
DID and blockchain have the potential to enable patients to access their identities and data, review and amend them, see who else has accessed data, give consent, or opt-in / opt-out of data sharing, get their data deleted, and even request they be forgotten.
There are two dimensions to the use of DID in healthcare, both related to data. The first part is the personal health information of an individual which is well controlled and defined by self-sovereign identity. The information also comes from devices the person is wearing, either on medical prescription or by personal choice.
The second dimension is any smart garment or device that can collect additional information about health, lifestyle, and physical activity provides data that can be linked as additional, nonqualified credentials. The two dimensions indicate the source and nature of information and are important since they put down the context of the use of DID in healthcare.
Below are the few healthcare initiatives with DID in the US that are valid in other parts of the world.
Precision medicine provides customization of healthcare in areas such as medical decisions, treatments, practices, and medicines, which are tailored to an individual. Precision medicine is critically dependent on healthcare data in near real-time, and of high quality. DID and blockchain enable innovative approaches for patients to handle their identities and data, engage them in their healthcare, and enable their participation in precision medicine.
The use of decentralized identifiers (DIDs) and verifiable credentials (VCs) data modeled by blockchain has made it possible to achieve entity authentication in a decentralized manner. It is possible to design a blockchain-based framework with DID for patient authentication and consent management for Electronic Health Records (EHR). It includes DID generation and authentication credential setup along with workflows for issuing and verifying credentials in the EHR ecosystem. Hyperledger Indy blockchain and Aries library are used to implement the framework.
One example here is Truu that is collaborating with National Health Service (NHS) to transform the way healthcare organizations in the UK verify staff identities, qualifications, and certifications with its portable, trusted digital ID for healthcare professionals. Evernym, Hedera, MediBloc, MedRec, Health-ID, and Tykn are some of the other leading companies offering DID solutions for healthcare.
Data associated with a DID enables healthcare providers to interact with patients. With a patientÔÇÖs consent, multiple data sets associated with the same DID can be easily consolidated. Claims can be associated with a DID and be verified and signed by the healthcare entity or other authority.
We can imagine a decentralized identity situation to authenticate with a healthcare service online for a (digital enabled) patient. It includes the following steps:
Key areas where DID can be leveraged to improve healthcare include outcomes for patients, providers, and government agencies. Given the risks and challenges of planning and implementing such integration, it is critical to ensure that fundamental systems are robust and inclusive in order to maintain the confidentiality and security of personal data. The design of identification systems will dictate which integration models are ideal for any given situation.
ChainyardÔÇÖs blockchain accelerators allow us to go from concept to complete proof in as little as six weeks. This includes a discovery workshop, solution design, development, and testing. We quickly build a solution that forms the foundation for a full business network.