Originally published at International Business Times. Read the full article.
A token is a digital twin of a physical object or service in a blockchain that provides undisputed ownership and provenance, reduces transaction costs, and enables transaction automation through smart contracts.
A token can represent anything ÔÇô a character in a game, airline ticket, work of art, coins, etc.
Real estate tokens, digital artwork, fashion, licenses and certifications, capital markets fundraising, sports moments, virtual worlds, gaming, and crypto collectibles are just some of the thriving use cases in tokenization.
The key messages are:
The benefits of tokenization, especially fractional ownership, transparency, increased liquidity, and improved security, create new opportunities for improving the value transfer systems.
New tokens are being created every day, from physical assets to intellectual properties.
Want to learn more about how tokenization is disrupting the financial industry. Talk to an expert.
The Value of NFTs and Their Impact on Blockchain
Non-fungible tokens, or NFTs, havenÔÇÖt changed the blockchain industry at its core. However, theyÔÇÖve had quite a positive impact on bringing more visibility to blockchain and its many uses.
Many people not involved in the blockchain industry have been introduced to NFT crypto-assets in the form of digital art. Although collectible art is certainly one use for these assets and their unique attributes, itÔÇÖs just one representation of the vast array of ways thatNFT and blockchainsolutions could change modern life.
For example,NFT ticketswould help cut down on counterfeit sales for sporting events, concerts, conventions, and more. Because NFTs canÔÇÖt be duplicated, the originals would be simple to verify. Plus, each┬áNFT ticket┬ácould be programmed via a smart contract to entitle the legitimate ticket┬áholder to special perks like free merchandise or exclusive gatherings.
NFTs are also heating up the video game industry, which shouldnÔÇÖt be a surprise. Many players would like to own the digital assets they purchase or earn while moving through a game. Using an┬áNFT-in-game┬ápremise, those players could retain ownership of any assets beyond the confines of the game. This would enable them to market or sell those assets for a profit later.
Real estate is yet another growth space for the NFT industry.Saving land contracts on NFTs can reduce crimes related to fabricated documents. Perhaps one day,NFTs for landinformation will lessen the need for costly legal intervention in cases of proving who owns which parcel.
The Multifaceted Value Proposition of Blockchain and NFTs
Of course, many people still arenÔÇÖt sure what makes NFTs particularly valuable. Even those who understand NFTs generally have a little trouble seeing their real-world applications.
So what is the value of an NFT? Below are some of the major reasons NFT and blockchaintechnology stir up so much discussion surrounding profitability and inherent value.
1. NFTs offer provenance and ownership.
Because the token (a.k.a., the NFT) on a blockchain canÔÇÖt be forged or 100% duplicated, it becomes its own authority. Someone who owns an original NFT doesnÔÇÖt need to go through a central authority to show the NFTÔÇÖs authenticity. Removing the need for someone in the middle to legitimize an NFT makes ownership and trading less cumbersome. Accordingly, the value saved is transferred to the value of the NFT.
2. The NFT industry is fostering buyer-seller efficiencies.
More and more, NFT holders can tap into global marketplaces when they want to sell their NFTs. Because NFTs have more liquidity than traditional assets, their holders can recoup investments more readily. Additionally, NFTs support fractional ownership, giving smaller investors access to larger investments by enabling them to own a ÔÇ£sliceÔÇØ rather than an entire asset.
3. Smart contracts can follow NFTs for life.
NFTs can be programmed with smart contracts. Consider the situation of a digital artist who programs an NFT with a smart contract. The smart contract may give the artist a percentage of any sales of the NFT. Consequently, every time the NFT changes hands, the smart contract terms would be enforced immediately.
4. Blockchain and NFTs offer decentralization with security.
By its very nature, blockchain requires none of the centralized entities controlling the markets and marketplaces the world currently relies on. Rather, blockchain and NFTsfoster decentralization and transparency. At the same time, they offer incredible levels of security that would have seemed unfathomable before the advent of blockchain ledgers.
5. NFTs build trust thatÔÇÖs often missing in transactional relationships.
Blockchain ensures a single version of the truth. Period. As a result, systems and assets like NFTs that are built on blockchain are trustworthy. Any transference of blockchain items can be handled with a high degree of trust. And again, thereÔÇÖs no need for a centralized authority to step in to fuel the trust factor. It just exists.
To be sure, NFTs ÔÇö and blockchain, for that matter ÔÇö are going through what can only be called the ÔÇ£hypeÔÇØ cycle. Very high expectations are being set for what┬áblockchain and NFTtechnology can and will do. No doubt, some people will be disillusioned along the way to blockchainÔÇÖs maturity. Nevertheless,┬áblockchain and NFTs┬áare positioned to have a significant and transformative effect on many industries beyond those that have tested the waters so far.
In the article titled “Transforming the business of Real Estate Assets through Tokenization“, we have summarized various types of real estate tokens, the challenges it solves, and areas one needs to be aware of when venturing into them. This article focuses on the real estate tokenization process and implementation.
The real estate tokenization process starts with two steps – identifying the deal type and defining the legal structure. Subsequently, implementation involves selecting blockchain technology for storing tokens and choosing a platform where investors can securely purchase digital assets after verifying KYC and AML requirements.
The process begins with deciding on the asset kind, shareholder type, jurisdiction, and relevant rules that have a crucial impact in this initial phase of structuring deals. Generally, issuers choose to tokenize an existing deal in order to provide liquidity to present investors before soliciting money for a new project. Asset owners determine the specific property (or properties) to be digitized. The key considerations in deal structuring would be time-period for ROI, cash on cash return, securing investments, and legal and business formations. These more important details along with specific features/ parameters like rental type, rent start date, neighborhood, year constructed, stories, bedroom/bath, and total units are considered in the process.
The ownership information recorded on paper is transferred to the blockchain during the digitization stage. Security tokens are stored in a distributed ledger, and various actions are encoded in smart contracts. A legal wrapper needs to be created over the individual property to securitize and form an investment vehicle; a step necessary to digitize real estate.
The most common structures are:
Real Estate Fund: A private equity firm invests in a portfolio of properties, and the token symbolizes fund units. Accredited investors or approved institutional purchasers may only leverage the dividends gained from the tokenized investment.
Real Estate Investment Trust (REIT): Investors can create digital shares in a REIT, and token holders have the same rights to the REIT’s operational revenue that traditional investors do today.
Project Finance: Tokenization is a highly effective method of generating funding for projects. Tokens are made available to consumers and accredited investors during this event. Here the token may represent the ownership or future right to use.
´╗┐Single asset Special Purpose Vehicle (SPV): Tokens represent shares of the SPV under this arrangement, usually a series LLC, for compliance with KYC/AML rules for LLCs, each token investor needs to be registered as a member of the LLC before investing.
After defining the legal structure, the next step is to choose the right technology. The process involves making four choices:
Selecting Blockchain / Token: This involves, choosing the Blockchain on which the token will be recorded, deciding on the token standard to be used, modeling the token data, and defining smart contracts to establish rules on transfer, limits, commissions, etc.
Primary / Secondary Marketplace: Choosing how initial tokens will be mined and provided during the initial offering and defining where and how investors will trade the tokens later.
Custody: Establishing a secure custody system for real estate, including proper maintenance and reporting of real-world updates.
´╗┐KYC/AML: Verifying investors within regulatory compliance on a periodic basis.
The token generation and distribution are the primary focus of this stage, where several payment options are offered when purchasing tokens. Investors may require a digital wallet, available on the web and mobile platforms, to store the tokens. Investors receive these tokens during a live sale.
Primary Distribution: Tokens are awarded to the investors through this procedure in return for investment capital this is also the first time the tokens are minted.
Post-Tokenization Management: This step includes processes for managing corporate activity, such as shareholder voting and dividend distribution. Smart contracts coded on the token can automate these procedures. Management of the tokens will continue after they have been issued until they reach maturity or redemption.
´╗┐Secondary Trading: Tokenization increases liquidity in secondary trading. A token holder can swap tokens with another investor on a marketplace, through an exchange, or over the counter.
Real estate tokenization has several advantages that make it a far more efficient investment option than any previously available ones.
We can expect Real Estate Tokenization to open the market for real estate assets enabling efficient movement of the funds and effective management of equity besides providing higher reliability, transparency, and security. Real estate tokenization would be the future of real estate assets with Blockchain technology as the underlying foundation and platform making it more robust, flexible, and secure when compared to the traditional models.
Given these advantages, it is no surprise that the RET market is estimated to become a $1.4-trillion market by 2026 (source). This potential can be fulfilled provided the technology is optimized to overcome existing hurdles and issues. Additionally, expert solution providers in tokenization have an important role in expanding the market and helping real estate players navigate the initial stages of tokenization and minimize the risks and costs associated with it.
Chainyard has vast experience in architecting, building, testing, securing, and operating blockchain-based solutions for some of the largest companies in the world in multiple domains: Supply Chain, Manufacturing, Transportation, Logistics, Banking and Trade Finance, Insurance, Healthcare, Retail, Government and Procurement. Read these customer success stories to find how Chainyard helped clients build enterprise-grade large blockchain-based technology solutions. Chainyard is instrumental in building a platform for procurement innovation, Trust Your Supplier, that enables suppliers to create and maintain a trusted digital identity and selectively share information with a vast network of buyers and partners. Read more here.
Everest Group announced the research report of Enterprise Blockchain Services PEAK Matrix® Assessment 2022 with detailed profiles and assessments of 23 IT service providers.
No surprises, Chainyard leads the Major ContendersÔÇÖ group. This designation is testimony to ChainyardÔÇÖs Digital Transformation Services blockchain offerings to facilitate enterprise business transformations.
Chainyard’s blockchain journey started in 2015, with the quality assurance of Hyperledger Fabric releases beginning with ÔÇ£Open Blockchain.ÔÇØ With the COVID-19 pandemic accelerating blockchain adoption, use case adoption has changed from the early prototype and test engagements to full-fledged enterprise business transformations and development of new ecosystems across the arts, real estate, digital credentials and decentralized finance.
Chainyard is a Hyperledger and Linux Foundation member with the Hyperledger Certified Service Provider designation, an infrastructure partner of OpenIDL, an IBM Silver Business Partner, and ConsenSys Development Partner.
You may read more about the availability of the report here -> Everest Group´╗┐.
Learn about how Chainyard can help you with your blockchain initiatives today. Schedule your complimentary consultation with a Chainyard blockchain expert!
Business process automation has become an essential part of digital transformation initiatives for enterprises. Almost all enterprise IT decision-makers cite process automation as a critical driver of innovation and necessary in achieving business outcomes. While automating business processes is gaining significant attention, are IT professionals investing enough in automating engineering functions related to Security and DevSecOps? Are they methodically addressing security automation to derive maximum benefits from it?
Commonly, organizations receive thousands or even millions of alerts each month that the security staff must monitor. They must guard a much larger attack surface now with the prevalence of several types of devices, apps, and cloud systems. Manually addressing these threats is almost impossible. Automation becomes increasingly necessary to defend the applications and infrastructure against threats that might slip through the cracks due to human error. In fact, according to a global security automation survey, 80% of surveyed organizations reported high or medium levels of automation in 2021.
This article guides security professionals through various potential areas of security automation and the critical role of DevSecOps in CI/CD pipelines.
Opportunities to automate security functions are limitless, like any other business area. However, a methodical approach to identifying automation areas, besides prioritizing the same based on the frequency of activities, is critical to the success of automation initiatives. The following classification can act as a broad guideline for security automation:
Identifying evasive attacks across security layers by consolidating data from the security environments is the goal of extended detection and response solutions (XDR), a critical method of security operations automation. XDR enables security analysts with data that helps them investigate and respond to various incidents, often directly integrated with standard security tools. Essential automation functions to ensure security across endpoints, networks, and cloud systems include:
A range of vulnerability assessments aims to protect against data breaches and ensure the availability of IT infrastructure. They determine if the system is vulnerable to any known vulnerabilities, give severity ratings to those vulnerabilities, and, if and when necessary, offer remediation or mitigation. The issues of a growing pool of vulnerabilities and limited time available to fix these vulnerabilities are addressed by automating vulnerability scanning. These scanners detect vulnerabilities in a variety of network assets, including servers, databases, applications, regulatory compliance, laptops, firewalls, printers, containers, and so on.
Automated management of responses by orchestrating several operations across security tools is the critical function of Security Orchestration, Automation, and Response (SOAR) methods. SOAR enables security teams to effectively triage alerts, respond quickly to cybersecurity events, and deploy an efficient incident response program. Three key areas of automation include:
As businesses move to public cloud environments that provide on-demand access to computing, networking, storage, databases, and apps, security automation becomes increasingly important. The possible security risks generated by manually setting security groups, networks, user access, firewalls, DNS names, and log shipping, among other things, are eliminated by automating infrastructure buildouts. Further, monitoring security configurations across numerous instances of resources across single, multiple, and hybrid cloud systems is another area where automation is quite helpful in a cloud context.
Providing more ownership to development teams in deploying and monitoring their applications is the goal of DevOps. Automation of provisioning servers and deploying applications is critical for DevOps success. Software applications are complex and can potentially have many security issues ranging from harmful code to misconfigured infrastructure/environments. Integrating security processes and, more importantly, automating them as part of the DevOps workflows is the goal of DevSecOps.
Integration of security automation into the CI/CD pipeline processes without adversely affecting development speed and quality is essential. Automation should enable uninterrupted security compliance checks within the continuous development workflow. Besides, as described in the previous sections, various automation areas apply to the Continuous Operations workflows. Critical automation activities include:
Focus on DevSecOps is increasing as per a survey conducted by GitLabs in 2021. DevOps teams are running more security scans than ever before: over half run SAST scans, 44% run DAST, and around 50% scan containers and dependencies. And 70% of security team members say security has shifted left.
As technology advances, the automation methods applicable for security processes also expand. Teams are leveraging advanced automation techniques on one side while also broadening the scope of automation. Following are the popular techniques followed by enterprises in security automation besides classic opportunistic script-driven automation:
It is worth noting that AI/ML is becoming a reality as the technology matures. It is not a surprise to learn that over 3 out of 4 IT executives in a cybersecurity survey conducted two years ago said that automation and AI maximized the efficiency of their security staff.
Our comprehensive services in Cyber Security and Cloud & DevOps help enterprises significantly enhance their security profile. The following customer success stories demonstrate how we applied advanced techniques for improving security and transforming DevOps:
With digital transformation becoming a strategic commitment for businesses, automation in different areas has gained an additional fillip as an enabler. It is now a core priority for all enterprises. Automation eliminates the hassle of repetitive tasks, reduces errors, and increases accuracies. In fact, close to three in four companies cited that they achieved success when automation was their strategic priority (source).
Cloud automation is one instance of automation that involves using automated tools and processes to execute workflows in a cloud environment that would otherwise have to be performed manually by engineers. It enables businesses to take advantage of cloud resources efficiently while avoiding the pitfalls of manual, error-prone workflows.
The global cloud automation market size is expected to triple in the next five years, from 2022 to 2027 (source)
Cloud automation can be used in a range of workflows and tasks. some of the key use cases are given below.
Cloud automation tools help configure virtual servers automatically by creating templates to define each virtual server’s configuration. Other cloud resources, such as network setups and storage buckets or volumes, can be configured automatically. These automation approaches help in agile provisioning of the required cloud infrastructure.
Releasing a new application from development environments to production environments is a critical use case of cloud automation. It becomes even more critical in a CI/CD process where teams make new releases each week. Application deployments are time-consuming besides being error-prone when done manually.
Operating enterprise workloads is time-consuming, repetitive, and painstaking with tasks such as sizing, provisioning, and configuring resources like virtual machines. These tasks are the perfect automation targets that make life easy for IT engineers besides making businesses efficient.
Monitoring cloud infrastructure with the ability to provide immediate responses to incidents is critical to ensuring optimal application performance. Most public clouds offer built-in monitoring solutions that automatically collect metrics from the cloud environment. They allow users to configure alerts based on predefined thresholds.
Administration of infrastructure, network, application, and users become complex in hybrid and multi-cloud environments. Further integration between on-premises and public cloud systems becomes critical in a few scenarios. Cloud automation programs synchronize assets between local data centers and cloud resources. They can automatically shift workloads to the cloud when local infrastructure faces resource limitations. It enables disaster recovery scenarios with a remote DR site mirroring the on-premises environment.
Automation can further unite hybrid and multi-cloud management under a single set of processes and policies to improve consistency, scalability, and speed.
Cloud automation is essential for DevOps maturity, and the two typically go together well. DevOps emphasizes automation and relies on practices such as automated infrastructure-as-code, continuous delivery, and tight feedback loops, all dependent on automation.
DevOps is an evolution of agile practices and applies the innovations of the agile approach to operations processes. It can be considered a missing piece of Agile since a few of its principles are realized when DevOps practices are employed. Cloud automation furthers the benefits and promise of DevOps in an agile environment.
Continuous improvement with timely feedback, a DevOps essential, can be achieved more easily with embedded automation across the workflows.
Automating the cloud security process enables organizations to quickly gather timely information, securing their cloud environments while reducing vulnerability risks. Areas of automation could include:
Cloud security automation can manage risk in time, effectively deal with complexity, and keep pace with changes in the IT environment.
Intelligent automation of cloud operations at scale is the role of AI/ML. Unlike basic script-based automation, machine learning algorithms can learn from operation patterns, make predictions, and mimic human-like remediation. The application of AI/ML can range from auto-detection of anomalies to auto-healing to cloud resource optimization.
AI/ML-driven automation to manage cloud operations is still an evolving field but will play a more significant role in the coming years.
Integrating disparate automation across services and clouds is the primary goal of cloud orchestration. It creates a cohesive workflow to help the business achieve its goals by connecting automated tasks. Infrastructure-as-a-code (IaaC) approach has taken orchestration to higher automation levels by bringing together a series of lower-level automation through configuration-driven techniques.
Cloud orchestration allows users to create an automation environment across the enterprise covering more teams, functions, cloud services, security, and compliance activities.
Several tools help in implementing cloud automation, broadly classified into two categories as follows:
Any large-scale cloud environment needs cloud automation, and it is one sure way to derive the utmost value out of the system. Management tasks that would otherwise consume tremendous time and resources get automated by cloud automation. This empowers organizations to update their cloud environments more quickly in response to business challenges.
Following customer success stories demonstrate how we applied automation techniques to transform cloud and DevOps:
Originally published at CEOWORLD MAGAZINE and written by Chainyard SVP Isaac Kunkel. Read the full article.
As the spending on┬áblockchain technology┬átotaled $6.6 billion┬áin 2021, more companies are figuring out how to get involved.┬á The exact┬áblockchain opportunities┬áare unique to each businessÔÇÖs existing ecosystems, stakeholders, and processes. The business model is critical; with a suitable business model, we see blockchain technology┬áeliminating 90% of redundant tasks, speeding up cycle time by 90%, and reducing administrative costs by half for most of these companies.
The article discusses 5 Ways to Discover Blockchain Opportunities, starting with understanding blockchain and new business models, getting buy-in from all stakeholders, finding the right technology partner, quantifying the business value to all participants, and finally, having a roadmap for continuous improvements.
Want to learn more about how blockchain is disrupting enterprises? Talk to an expert.
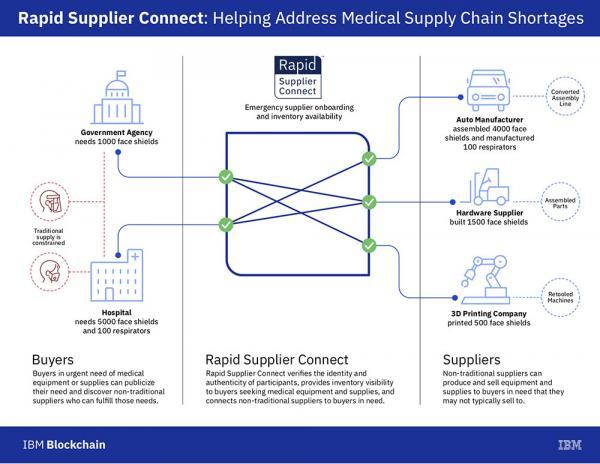
Real-time insight into a volatile and uncertain supply chain is never simple, and with the challenges of the current global situation, IBM harnessed the┬áTrust Your Supplier┬áblockchain-based┬áidentity platform built by┬áChainyardÔäó for qualification and identification, in conjunction with its existing┬áSterling Supply Chain Suite┬áand highly scalable┬áInventory Visibility┬ámicroservice to deliver this increased visibility.
This article was originally published on┬á´╗┐due.com┬á┬áand republished on┬áNASDAQ
To everyoneÔÇÖs great frustration, the course of COVID-19 and its enduring economic impacts look unpredictable. As companies┬árush to aid the COVID-19 response or fight to keep their doors open, they require trust in suppliers and partners and transparency into┬ásupply chains and contractual obligations. Luckily, blockchain excels on both fronts.
The article suggests three strategies to effectively add blockchain to your own recovery effort.
This article was originally published on Silicon Angle
As the world becomes more digital as the coronavirus pandemic forces many to work remotely, companies and individuals need to share more and more data. This sharing can be more efficient if the data and the sources that provide it are confirmed, verified and trusted.
ThatÔÇÖs why computing giant IBM Corp. is betting on blockchain as a solution for now ÔÇôand for the future.
ÔÇ£Blockchain brings a platform for trusted data exchange while preserving privacy,ÔÇØ said┬áJerry Cuomo┬á(pictured), vice president of blockchain technology at IBM Corp. and an IBM fellow. ÔÇ£And that provides a foundation to do some amazing things┬áin this time of crisis.ÔÇØ
Cuomo spoke with┬áDave Vellante, host of theCUBE, SiliconANGLE MediaÔÇÖs mobile livestreaming studio, during the┬áIBM Think Digital Event Experience. They discussed the importance of blockchain in the digital world, as well as some applications of the technology during the coronavirus pandemic.┬á(* Disclosure below.)
IBM was one of the first blockchain providers and has more than 1,000 customers now using┬áits┬áIBM Blockchain Platform, which is powered by The Linux FoundationÔÇÖs┬áopen-source Hyperledger Fabric. Among these users, more than 100 have created production networks, according to Cuomo.
ÔÇ£ItÔÇÖs been great to see┬ásome of the proprietors of those networks now repurpose the networkÔÇÖs towards hastening the relief┬áof the COVID,ÔÇØ he said.
One of the applications of blockchain during the pandemic has been to┬ácombat supply shortages. Because of the lockdown caused by the crisis, some suppliers were left without key goods, and buyers realized the need to expand the network of providers of these products very quickly.┬áHowever, current laws and regulations can cause a new supplierÔÇÖs integration into the network to take many weeks.
ÔÇ£In IBM, for example, we have over 20,000 suppliers┬áto our business, and it takes 30 to 40 days to validate┬áand verify one of those suppliers,ÔÇØ Cuomo said. ÔÇ£We donÔÇÖt have 30 to 45┬ádays ÔǪ think about a healthcare company┬áor a food company.ÔÇØ
To shorten this process, IBM used the Trust Your Supplier blockchain-based identity platform built by Chainyard Supplier Management Inc.
ÔÇ£If they [suppliers] are part┬áof the Trust Your Supplier network,┬áand theyÔÇÖve already onboarded to IBM,┬átheyÔÇÖre well on their way to being visible to all of these┬áother buyers that are part of the IBM network,ÔÇØ Cuomo┬áexplained. ÔÇ£And instead of taking 40 days,┬ámaybe it only takes five days.ÔÇØ
Another blockchain use case focuses on aggregating valid data to help authorities fight the pandemic. The idea is to tackle one of the main problems that scientists and researchers face when trying to map and contain the crisis, which is the lack of integration of verified data sources that can be used with confidence.
To help solve this problem, the IBM Blockchain team joined the MiPasa project, from enterprise-grade blockchain platform Hacera, in creating a verified data hub.
ÔÇ£With MiPasa being a data hub┬áfor verified information related to the┬ácoronavirus, [it is] really laying a foundation now for a new class┬áof application that can mash up information to create new┬áinsights,ÔÇØ Cuomo explained. ÔÇ£Perhaps applying artificial intelligence and machine┬álearning to really look not just at any one of those data┬ásources, but now to look across data sources and start to make┬ásome informed decision.ÔÇØ
A third application of blockchain in this pandemic is for digital identity verification. ÔÇ£YouÔÇÖre working remotely; youÔÇÖre using tools like Zoom; thereÔÇÖs a huge spike in calls and online requests┬áfrom telehealth or government benefit programs,ÔÇØ Cuomo said.┬áÔÇ£So, this is all happening and everything behind the scenes is: ÔÇÿIs this user who they say they are?ÔÇÖÔÇØ
The Verified.Me solution by SecureKey Technologies Inc., which runs on IBM Blockchain, aims to facilitate identity verification. It allows users, through a mobile application, to invite institutions to represent and verify them. Users control their own information and the terms and conditions under which it will be used.
ÔÇ£The provider doesnÔÇÖt know who the requester is, requester┬ádoesnÔÇÖt know who the provider is ÔÇö that is double blind.┬áAnd then the network provider doesnÔÇÖt know either,ÔÇØ Cuomo explained. ÔÇ£But somehow trust is formed, and thatÔÇÖs the magic of blockchain, allowing that to happen.ÔÇØ